RusRoute firewall 2.0.1
Description of the fast start for the program is here
RusRoute demo video of installation and configuration.
Help for the program “RusRoute” (routing firewall, Internet gateway).
 RusRoute firewall 2.8.1
RusRoute firewall 2.8.1
Table of contents
1. Purpose of program.
2. System requirements.
3. Program installation.
4. Program activation.
4.1. What offers activating the demo-version of program.
4.2. What offers activating the full version of program.
4.3. Activation.
5. Licence agreement.
6. Program dialogs description.
6.1. "About" page.
6.2. Settings page.
6.3. "Network info" group-page.
6.3.1. Network adapters.
6.3.2. Routing table.
6.3.3. Arp table.
6.4. "Lists" group-page.
6.4.1. Adapters lists.
6.4.2. IP addresses lists.
6.4.3. Network protocols.
6.4.4. Time table.
6.5. DHCP servers.
6.6. TCP congestion control.
6.7. HTTP cache.
6.8. Filters data.
6.9. Billing schemes.
6.10. Journals.
6.11. Users.
6.11.1. User info dialog.
6.12. Shapers.
6.13. Cron tab page.
6.14. Firewall rules.
6.14.1. Firewall rules wizard.
6.15. "VPN" group page.
6.15.1. VPN role.
6.15.2. VPN users.
6.16. TCP connections.
6.17. UDP dynamics.
6.18. Logs.
6.18.1. Http logs.
6.18.2. Ftp logs.
6.18.3. Dns logs.
6.18.4. Common log.
7. Technical support for the program.
1. Purpose of program.
RusRoute (routing firewall, Internet gateway) - is the ideal solution to make a Internet gateway for local area network (LAN) of any firm, monitoring and restricting user’s traffic, protecting against network attacks by having NAT functions, redirect, shaper, VPN, proxy, LAN to VPN Bridge, HTTP cache, DHCP servers, timed action and Splitters for rules.
The program consists of two modules: one is the driver for intercepting Ethernet and IP packets (packets of Internet protocol version 4 - IPv4) and passing them to the second module: the firewall module.
Firewall module is the most intellectual part of product, which provides route link for packets between networks with additional functions such as
- traffic routing
- NAT - network address and port translation
- redirect
- shaper
- VPN
- proxy
- LAN to VPN Bridge
- HTTP cache
- DHCP servers
- packets filtering of network protocols in accordance with given rules, time, with splitting outgoing routes.
- authorization, authentication, accounting and billing of users (entering into RusRoute system, giving user access right for using network resources, creating statistics for traffic counting and money spent by each user).
2. System requirements.
The program can run under Windows 7/8/8.1/10 / Server 2008 R2/2012 R2/2016/2019, 32/64 bits. Minimal requirements for hardware components are: Pentium 1000 MHz, 512 Mb of RAM, Ethernet 10/100 Mbytes/s, Internet Ethernet connection such as ADSL or ETTH, 3G modem or other Ethernet-compatible controller.
Hardware requirements gets higher in direct proportion an increased number of active connections, number of active users and necessary speed.
3. Program installation.
Run setup to install the program, read licence agreement and follow instruction steps to set up the program.
Setup will ask for replacement of files by the new version of files, if the installation is done over a previous version. After extracting necessary files, the module program of the firewall is started and will install the required driver for your operating system.
Then you needed to go to the About page to enter registration data (user name, e-mail address and program serial number), after that to choose "Verify key and generate activation request" from data list of registration menu.
The message "key is valid" will appear if the serial number is entered correctly.
Now you can copy activation request to your clipboard and send it to our support e-mail support@rusroute.com or you can choose to send your activation request later.
You probably need to use your administration user on order for get the firewall working correctly (It will be necessary when you manually restart your firewall).
It’s required to set up your configuration and activate the key.
Predefined configuration is not ready to use it. To set up a configuration for a particular application consists of using firewall Wizard, edit lists and rules, add users, change billing schemes, and make other optional changes, then turn RusRoute firewall on on the "Settings" page.
The disabling standard Windows firewall is a better way to RusRoute firewall work.
4. Program activation.
4.1. What offers activating the demo-version of program.
Demo-version activation allows you to use the program for 60 days (compared to 30 days without activation) in order to evaluate it. But you must activae it the 30-days period expires.
4.2. What offers activating the full version of program.
Activating the full version program allows you to have a certain number of users (working at the same time in the system) for which the program was purchased (it is defined by pair: serial number and activation code).
4.3. Activation.
To activate your program you must send an activation request to support e-mail support@rusroute.com. Activation request is generated by RusRoute program when verifying your key in the “About” page. The text with your activation code received from support team must be copied to clipboard and pasted in the context menu in the same "About" page, then you must choose from the menu "Verify key and activation code". When you’re done, you will see an appropriate message and number of users available in the system.
5. Licence agreement.
The licence is defined by the serial number and activation code. The type of licence is defined by the number of users working at the same time in the system. The originality of user is defined by its IP address. Therefore, the number of users represents the number of authorized IP addresses in the system. Note: if the login to RusRoute system was made through a firewalled computer from local addresses 127.0.0.1 (throw web interface), then this user will correspond to a number of IP addresses (IP addresses of all network adapters on computer). You should take this into account when choosing the number of users when purchasing RusRoute. At the same time, if the user authorization working on the firewalled computer is automatic by firewall address, then when any sort of activity begins, any firewall IP address is automatically given to the user if this address isn’t yet used in the system. Usually the number of local firewall IP adresses is not high (less than 3-5).
END USER LICENCE AGREEMENT
The present licence agreement is a public offer and consists of all main conditions of Your (hereinafter referred to as «User») use of “RusRoute firewall” program (hereinafter referred to as «Program») for computer.
The Author - citizen of the Russian Federation, Moiseenko Andrey Alekseevitch (hereinafter referred to as «Right holder»), in accordance with current agreement, is the holder of exclusive material copyright for “RusRoute firewall” program, including User manual for it in hardcopy and/or electronic copy and is obligated to allow User (direct or through authorized third hand) unexceptional right for using Program, with restrictions of installation rights and starting Program in accordance of set up by current rules and conditions of Licence agreement (the simple unexceptional licence).
Order of offer acceptance (Licence agreement)
The current offer (licence agreement) is considered to be accepted by User through the following conditions:
1) Through clicking the «Accept» button while setting up the Program and pressing «Install», the User agrees unquestionably to User agreement with current agreement rules.
2) Through order, payment or receive by User of unexceptional rights for using Program on the currently offered confitions (agreement) from Rightholder or authorized third hand people it means unquestioning the User agreement with conditions of current licence agreement.
Transferring order and costs of unexceptional rights
In accordance to current Licence agreement, User must give in 30 days from offer acceptance from Rightholder (in direct way of through authorized third hand people) unexceptional rights for using Program. The moment of transferring to User unexceptional rights is considered the moment of Rightholder's (or third hand people making right transfer) hand on a document in accordance statement. The user must pay a fixed fee for rights; the amount of fee is defined by conditions of Licence agreement with the party, agreeing upon rights transfer. In case of User cancellation (not to giving rights in the specified time) the current Licence agreement is considered not to have ended.
Program rules
User has the right to use Program in the any country of world in accordance with conditions of current Licence agreement as long as usage is in accordance with the following rules:
1. Recompilation and/or modification of Program is prohibited.
2. To lease or rent, temporary use of Program for others is prohibited.
3. To split Program by parts to use it on different computers is prohibited.
4. Using the Program with the purpose to create malicious program data or codes is strictly prohibited.
5. Using the Program in a way that conflicts with the laws of the Russian Federation is strictly prohibited.
User’s rights
To use Program for evaluation purpose in 30 days from its first start (install).
To Make copy of program under condition that the copy is aimed for archiving goals and to replace legally obtained distribution if the original is lost, removed, or stand unsuitable for using. The copy mentioned in this paragraph cannot be used for other purposes and must be removed if the using of Program by User ceases to be rightful.
Rights disclaimer
Right holder does not guarantee the usability of Program while breaking conditions described in User manual, and in the case of violation of User the conditions of current Licence agreement.
User takes upon themselves the risk of accordance of Program by his wishes and needs, as soon as risk of accordance the conditions and value of giving rights by his wishes and needs.
Right holder and/or his pairs are not to account for any damage or loss of profit, independently of appearance causes, (including, and not restricted by this, special, fortuitous, incidental or indirect damage, profit loss, interrupting commercial or production activity, business information loss, negligence, or any other loss), that appears when using Program or impossibility to use it.
Final rules
Validity period of current offer conditions (Licence agreement) are from June 20, 2020, to June 20, 2025.
In case of infringement on the author's rights for the Program, the violator is solely responsible for conduct that could constitute a criminal offense, give rise to civil liability and administrative responsibility or otherwise violate any applicable law or regulation of the Russian Federation or any other local, state, national or international laws.
Program site: http://rusroute.com
Support at e-mail: support@rusroute.com
Demo key: RR-0001-Demo-6167-520B-434F-822D-F126
© 2007-2022 Moiseenko A.A., All rights reserved.
6. Program dialogs description.
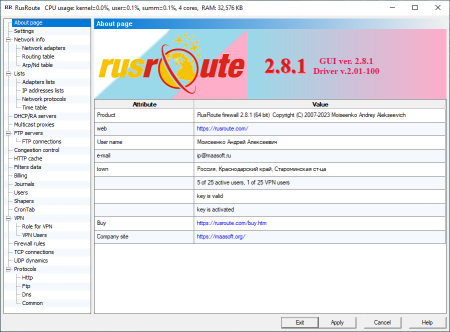
6.1. "About" page.
 About
About
In this window you can view the product name, its version, copyrights, web-site of program, registration data of user (user name, e-mail address, serial number), program working mode, number of active users and serial number, and activation code check status.
By double clicking your mouse or pressing F2 key, you can change the user registration information.
By pressing the right mouse button on the list you will access the menu. In the menu you have step by step options to register the program. The registration info can be entered as soon as setup is finished or you can do it later. You can also modify this info later on. You can delay sending the activation request and entering activation code. For example, you can do this after rebooting your computer and set up minimal program configuration: lists, users, rules.
6.2. Settings page.
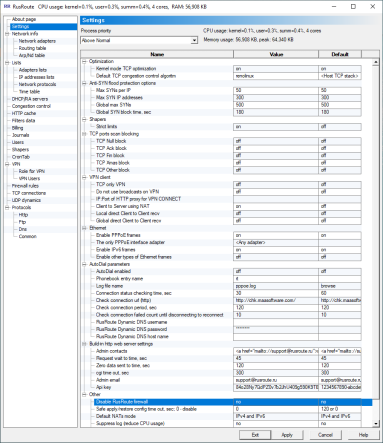 Settings of RusRoute firewall
Settings of RusRoute firewall
You can view the global settings of the program in this window such as process priority, Kernel mode TCP optimization, default TCP congestion control and avoidance algorithm, Anti-SYN flood settings, Shapers settings, blocking of TCP scan attacks and specific VPN client setting. You can view here the memory size used by RusRoute.
Turning on the kernel mode TCP optimization allows you to rapidly reduce processor usage because that part of the TCP packets handling is moved from user mode to kernel mode.
Turning on strict limits for TCP shapers permits you to handle strict speed limits instead of non-strict mode, when RusRoute is trying to use full bandwidth of root shapers for sub-shapers.
6.3. "Network info" group page.
6.3.1. Network adapters.
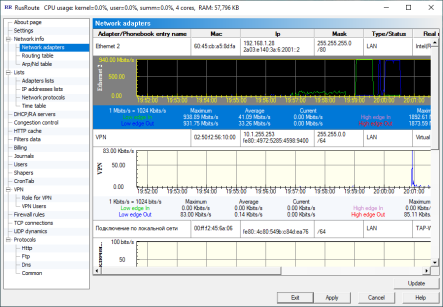 NetworkAdapters
NetworkAdapters
Here you can view the list of network adapters of operation system, both existent and inactive or removed. Some adapter characteristics are also shown here. Phonebook entries are shown here too.
Adapter characteristics represent parameters as follows: name (form network places properties), Mac address, IP address, subnet mask, type/status, real name, Mac address of peer (for WAN connections), Server IP address (for WAN connections).
If the serial number is not right or expired or if the driver is not installed correctly, the adapter name is defined as , and will not function.
You can refresh the adapter list, for example, if you have renamed an adapter.
6.3.2. Routing table.
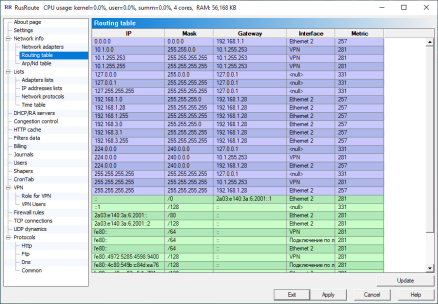 RoutingTable
RoutingTable
You will find here the standard operations to use the system routing table. The list contains the following fields: IP address, mask, gateway, interface (adapter name, for local loopback is "null nic"), metric.
You can update this information manually by pressing "Update" button as done in the previous page. Usually you don’t have to do this because operation system when starting Windows XP is setting-notification events about routing table changes.
6.3.3. Arp table.
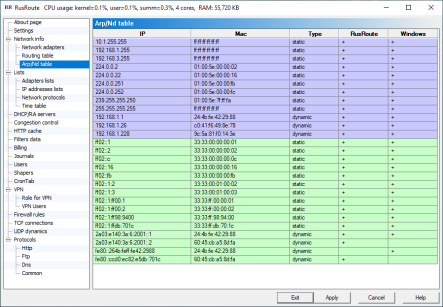 ArpTable
ArpTable
The Arp (Address resolution protocol) table is shown in this window. It is also known as MAC addresses table. These are dynamic and static records for mapping IP addresses to correspondence MAC addresses of network adapters. RusRoute has its own Arp table in addition to Windows Arp table. You can view it in last two columns if the record of table is open in RusRoute and/or Windows Arp table.
To protect from network attacks of IP spoofing inside local network, you can add static records to the table. You can easily do this by creating *.bat file with commands type as
arp -s ...... and setting this file to run at Windows start up. You can copy the contents of the bat-file lines to clipboard from this Arp table page by pressing right mouse button and selecting appropriate menu item.
You can access more information about the Arp command in Windows’ documentation and by using command arp /? from the command line.
6.4. "Lists" group page.
Here are the lists used for firewall rules. Every list is settable by some fields. You can sort list by pressing the header button.
6.4.1. Adapters lists.
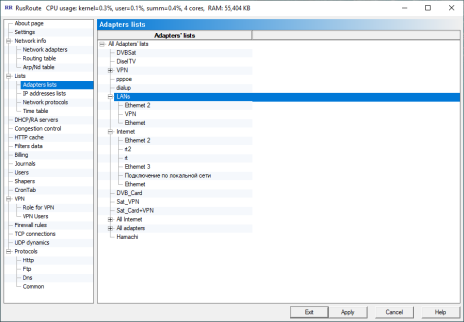 AdaptersLists
AdaptersLists
Here you can create or modify adapters lists. For this press the right mouse button on existent elements and select what you need from the menu.
6.4.2. IP addresses lists.
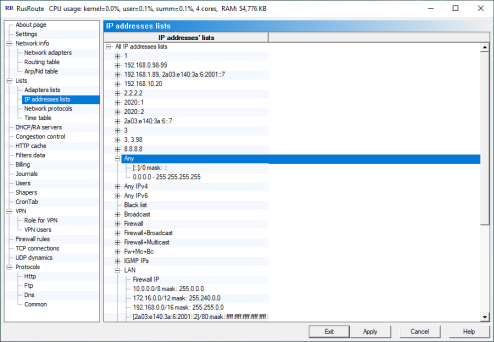 IpAddressesLists
IpAddressesLists 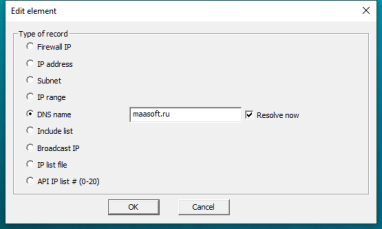 IpAddressesListElement
IpAddressesListElement
Here you can create and modify IP addresses lists. To do this, use the right mouse button on existent elements and select what you need from the menu. The field for choosing element type and writing down element value is used. The elements of every list can be the next types:
- "Firewall IP" - any IP address of firewall,
- "IP address" - address, typed by hand,
- "Subnet" - subnet, assigned by IP address and subnet mask,
- "IP range" - IP addresses range from start to end (using arithmetic comparison
- "DNS name" - dns name of host, for example, "www.microsoft.com". Firewall is working directly with IP addresses, therefore it is important to define IP address/es by domain name in order to make it work. If you don’t do this soon by un-checking "Resolve now" button, you can resolve them for all domain names from lists by selecting appropriate context menu item from main window.
- "Include list" - merges list with other list.
6.4.3. Network protocols.
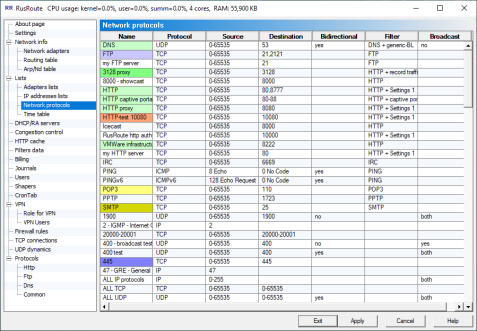 NetworkProtocolsList
NetworkProtocolsList
Network protocols list with the next fields: name, IP protocol, (port) source, (port) destination, bi-directional (for UDP and PING), filter, filter data, broadcast.
Supporting filters for the next protocols: FTP(both active and passive modes), IRC, PING, HTTP. For HTTP filter you can use filter data settings such as caching.
6.4.4. Time table.
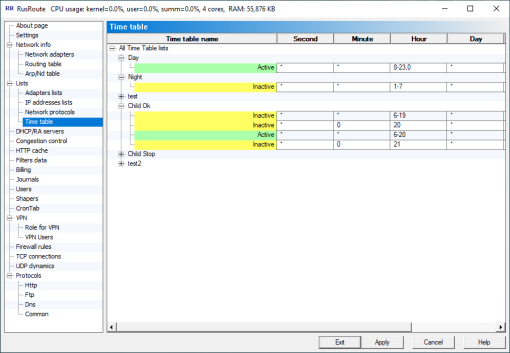 TimeTable
TimeTable
Here you can configure the time table lists to use them within firewall rules parameters. According rule will be active while connection attempt in time interval specified only. The rule will be ignored in the other time, but the already available connection will be active up to closing.
6.5. DHCP servers.
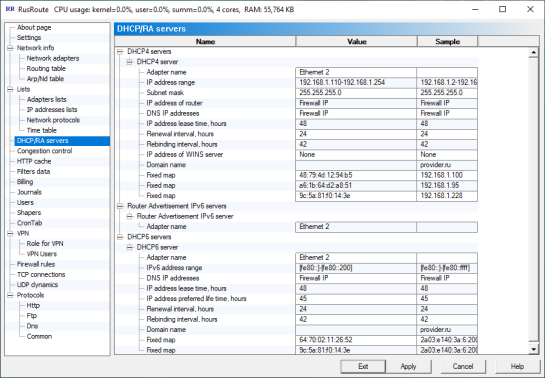 DHCPservers
DHCPservers
You can create DHCP servers on any Ethernet adapter. DHCP servers are used not to set up IP addresses and other network parameters on every computer of connected network.
You can set up here direct map between particularly allocated MAC address of network card and IP address.
6.6. Servers for TCP transmission congestion control and avoidance algorithms (is obsolated for 2.x version for RusRote firewall and unused).
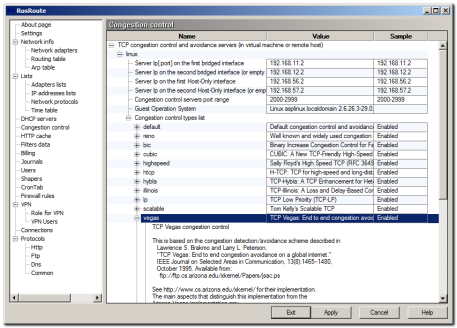 TCPCCServers
TCPCCServers
You can configure external TCP servers with different algorithms of TCP transmission control; such algorithms are named TCP congestion control and also avoidance algorithms.
The idea and implementation are based on the fact that RusRoute can redirect both incoming and outgoing TCP connections to other IP addresses and ports. If you start virtual machine with the Linux operation system with using freeware VirtualBox 3.0.8 package, for example, http://www.virtualbox.org/ or more powerful and free VMWare Server http://www.vmware.com/ (or set up Linux on the stand alone computer connected to RusRoute firewall server with analogous network connection settings), than redirecting TCP packets (for incoming connections) to the virtual Linux machine at first, which is setting up specific congestion control and avoidance algorithm and makes redirection of that connection data in a client-server sockets application backwards to the IP address of RusRoute, telling IP addresses and port numbers of source and destination in the first 12 bytes of connection (for further identification), than that Linux is the main who is a connection supervisor for incoming connections. The "incoming" means here the primary level of TCP connection (see RusRoute firewall special rules settings for further explanations). A similar way is for outgoing connections: RusRoute firewall is connecting to a Linux server transferring the first block of parameters - IP address and port to connect by Linux application, which will be sent by Linux to using the other network interface to be intercepted and redirected by RusRoute to the real end point address, using simple IP and port substitution. For a successful connection, the Linux server is returning code 0 (4 bytes, word) as the first data, RusRoute is extracting that data and other data are transferred transparently in both directions. If a connection error appears, the server is sending successive 4 bytes - error code, 4 bytes - error message length (must be the less than 512 bytes in current implementation), the error message of the given length, and closing the connection. RusRoute is making TCP Reset reply to initiator of connection which leads to the "Connection refused" reaction, unless the connection was not closed before by time out. The error message is displayed in RusRoute common log window for diagnostics.
Client-server application for making such network interconnection is placed in data\cctcp folder of installation, it is distributed as a static binary compiled files for Windows (it is using single stack only) and 32 and 64 bits versions of Linux. In the case you are interesting in you can get cctcp source codes by additional request. You can experiment with the TCP stack substitution by stack of other Windows OS, for example, the TCP stacks of Windows XP and 2003 Server are differed from the new Microsoft TCP stack first introduced in Windows Vista and implemented in Windows Seven and 2008 Server. You can download the latest version of cctcp TCP congestion control program (32 and 64 bits versions) with configs for xubuntu 9.10 from cctcp_static_linux_binaries_32_64.tar.gz location.
Conditions of use - as a part of RusRoute distribution in accordance with RusRoute licence agreement.
For optimization, simple using and interraction RusRoute with Linux skipping RusRoute driver, I am connecting the virtual machine by two virtual network interfaces.
For optimization, simply use and interaction RusRoute with Linux skipping RusRoute driver; I am connecting the virtual machine by two virtual network interfaces.
You can create such network adapters by adding host-only adapter by VMWare virtual networks manager; I am setting fixed MAC addresses for Guest network adapters too.
I am un-checking the check box from RusRoute driver network adapter settings for one host-only adapter.
The second adapter is created in the same manner, and network interface with default routing to RusRoute IP address is turned up.
The next improvements of work can be achieved by traffic splitting for incoming and outgoing connections to different virtual adapters (for eliminating speed limit of 100 Mbytes/sec divided by two, because the same data is received and sent in both direction usually, and maximum speed can be limited by 1/2 factor).
For that you can add one more network adapter for direct data transfer (with RusRoute driver unchecked in the adapter settings) and one more host-only adapter for virtual routing. In this case, you should to create additional routes.
For example, we have 2 adapters for direct communication with the names of VMnet1, VMnet2 and VMnet8 (unused), and 2 for routing with the names of VMnet3 and VMnet4, (you can add VMnet5 for local tests).
Then we make the IP address assignment on VMnet1
192.168.21.0/24 :
192.168.21.1 - for RusRoute
192.168.21.2 - for Linux (usual network)
On the VMNet2 -
192.168.22.0/24 :
192.168.22.1 - for RusRoute
192.168.22.2 - for Linux
(usual network)
On the VMnet3 -
192.168.23.0/24 :
192.168.23.1 - for RusRoute
192.168.23.2 - for Linux
and routes
1.0.0.0/16 with 192.168.23.1 gateway,
0.0.0.0/0 (default) for 192.168.23.1 gateway (not necessarily required; it’s used in order to set Linux Internet network connections, if they are need)
On the VMnet4 -
192.168.24.0/24 :
192.168.24.1 - for RusRoute
192.168.24.2 - for Linux
and a route
1.1.0.0/16 to a 192.168.24.1 gateway
Configuration files for my installation of ASPLinux 14 are as follows:
/etc/sysconfig/network-scripts/ifcfg-eth0 :
# Advanced Micro Devices [AMD] 79c970 [PCnet32 LANCE]
DEVICE=eth0
BOOTPROTO=static
BROADCAST=192.168.21.255
HWADDR=00:50:56:00:21:02
IPADDR=192.168.21.2
NETMASK=255.255.255.0
NETWORK=192.168.21.0
ONBOOT=yes
NM_CONTROLLED=
/etc/sysconfig/network-scripts/ifcfg-eth1 :
# Advanced Micro Devices [AMD] 79c970 [PCnet32 LANCE]
DEVICE=eth1
BOOTPROTO=static
BROADCAST=192.168.22.255
HWADDR=00:50:56:00:22:02
IPADDR=192.168.22.2
NETMASK=255.255.255.0
NETWORK=192.168.22.0
ONBOOT=yes
NM_CONTROLLED=
/etc/sysconfig/network-scripts/ifcfg-eth2 :
# Advanced Micro Devices [AMD] 79c970 [PCnet32 LANCE]
DEVICE=eth2
BOOTPROTO=static
BROADCAST=192.168.23.255
HWADDR=00:50:56:00:23:02
IPADDR=192.168.23.2
NETMASK=255.255.255.0
NETWORK=192.168.23.0
ONBOOT=yes
NM_CONTROLLED=
/etc/sysconfig/network-scripts/ifcfg-eth3 :
# Advanced Micro Devices [AMD] 79c970 [PCnet32 LANCE]
DEVICE=eth3
BOOTPROTO=static
BROADCAST=192.168.24.255
HWADDR=00:50:56:00:24:02
IPADDR=192.168.24.2
NETMASK=255.255.255.0
NETWORK=192.168.24.0
ONBOOT=yes
NM_CONTROLLED=
/etc/sysconfig/network-scripts/ifcfg-eth4 :
# Advanced Micro Devices [AMD] 79c970 [PCnet32 LANCE]
DEVICE=eth4
BOOTPROTO=static
BROADCAST=192.168.25.255
HWADDR=00:50:56:00:25:02
IPADDR=192.168.25.2
NETMASK=255.255.255.0
NETWORK=192.168.25.0
ONBOOT=yes
NM_CONTROLLED=
/etc/sysconfig/network-scripts/route-eth2 :
1.0.0.0/16 via 192.168.23.1 dev eth2
default via 192.168.23.1 dev eth2
/etc/sysconfig/network-scripts/route-eth3 :
1.1.0.0/16 via 192.168.24.1 dev eth3
ubuntu 9.10 network config file for cctcp server addresses 192.168.2*.2
#
# /etc/network/interfaces config file for ubuntu for RusRoute tcp congestion control support
#
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet static
address 192.168.21.2
netmask 255.255.255.0
auto eth1
iface eth1 inet static
address 192.168.22.2
netmask 255.255.255.0
auto eth2
iface eth2 inet static
address 192.168.23.2
netmask 255.255.255.0
up ip route add 1.0.0.0/16 via 192.168.23.1
up ip route add 0.0.0.0/0 via 192.168.23.1
auto eth3
iface eth3 inet static
address 192.168.24.2
netmask 255.255.255.0
up ip route add 1.1.0.0/16 via 192.168.24.1
auto eth4
iface eth4 inet static
address 192.168.25.2
netmask 255.255.255.0
/root/cctcp/cclist.xml is supplied with the sources, the template can be generated by command
./cctcp.out -writeconfig
/root/cctcp/cctcp (starts the compiled cctcp.out file) :
#!/bin/sh
cd /root/cctcp
/etc/rc.d/init.d/network restart
killall -9 cctcp.out
./cctcp.out -system "`uname -a`" >/dev/null &
#./cctcp.out 10077 -system "`uname -a`" >/dev/null &
In /etc/rc.d/rc.local I was add the lines
setterm -blank 0
/root/cctcp/cctcp
You need to start the cctcp.out program compiled with the root access rights for using all of available TCP stack modifications of Linux.
The current Linux kernels are supporting the next TCP algorithms:
"reno", "bic", "cubic", "highspeed", "htcp", "hybla", "illinois", "lp", "scalable", "vegas", "veno", "westwood", "yeah".
Your network quality is depends on different factors. For example, I observed for a long time the strange effect of a stable but very slow speed (300 KBytes/sec) of receiving data to two computers with Windows 7 RC (both x64 and i386) from computers with Windows XP inside a local area network (i.e. between the different TCP stacks of Windows). The first test using of above technology was recorded a speed up by 19 times to 5700 - 5900 Kbytes/sec.
Later, 26 October 2009 I did some new tests and the results were looking modest - 1071 KB/sec (without RusRoute) and 4143 KB/sec with using reno/linux stack. And four days later (30 October 2009) the slowdown was self eliminated but returned later. The tests were done in a network isolated from main network by switching hub 3Com 100 Mbytes/sec full duplex, network cards were working t 100 Mbytes/sec half duplex. Data transfer speed between two Windows XP’ was fast enough. The Windows OS updates weren’t performed those days (26-30 October), with a possible exception of Symantec Antivirus updates on Windows XP computers.
A better option can be using of alternative TCP stacks for interconnecting with the external network such as Internet or between remote filial or buildings of corporate network, or using old stack (XP/2003) conversion for a long distance global networks.
The usual using of Linux stacks can give more speed results in the case of using of RusRoute technology too, because of lowering generic network adapter utilization with minimum resource allocation for Guest Linux OS.
6.7. HTTP cache.
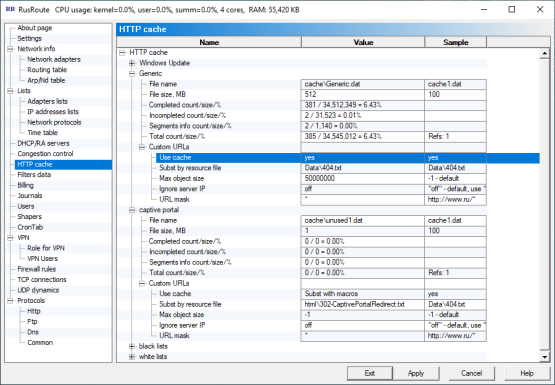 HTTPcache
HTTPcache
You can make here HTTP caches with specific name and size to avoid downloading each time for every computer the same updates from the Internet and pages, pictures and other content which was not modified on the web server since first request was made. You can subset the server responses for some requests matched by mask specified by your data files (we recommend to prep end the HTTP/1.1 header to a resource data file with out of "Connection: " and "Proxy-Connection: " fields; you can use "%" in such headers as a parameter of "Content-Length: ", "Last-Modified: ", "Date: ", "Content-Type: " to automatically define by value , use macros "{URL}", "{Base64Url}", "{HTTPDOMAIN}", "{HTTPURLPATH}", "{FirewallIp}" and some others. If RusRoute program will not find the header, than it will insert some standard "HTTP/1.1 200 OK" header) You can select "skip" to go to the next cache mask comparison or "no" to not cache that request.
You can do perform some actions with the cache such as "Add new custom URLs", "Remove incomplete", "Cleanup cache". This page also shows cache statistics.
6.8. Filters data.
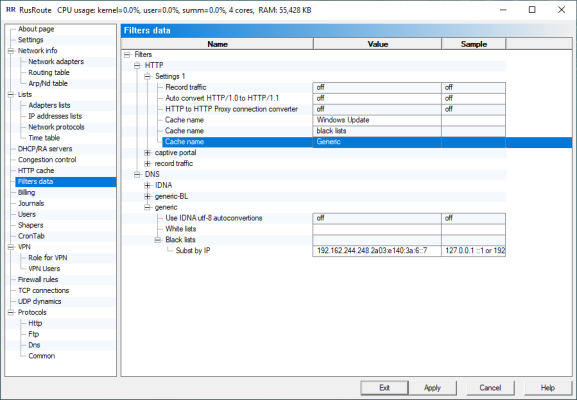 FiltersData
FiltersData
You can set up here variable parameters of filters with specific name. The example is using caches of HTTP, transparent HTTP to HTTP proxy connection converter (which work in conjuncture with cache, even when caching function is disabled).
6.9. Billing schemes.
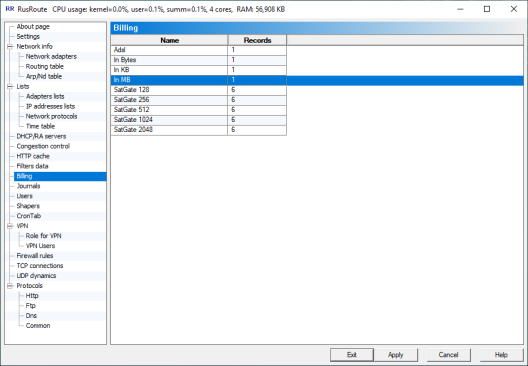 BillingShemeList
BillingShemeList 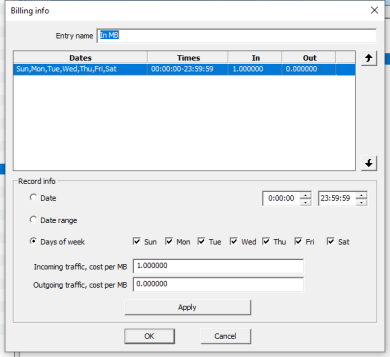 BillingShemeExample
BillingShemeExample
Here you can create and edit different billing schemes, that are rules in accordance with the balance of a user changes. Billing is different by days, day ranges, days of the week with intersection of time intervals during days.
If you set up traffic cost 1.000 per megabyte then such billing scheme encounters a negative traffic in megabytes. If 1024.000 than is kilobytes, then 1048576.000 is in bytes.
The value of cost can be set up negatively, in this case traffic encountering is making isn’t negative, but minimum allowable balance value is missing.
The edition of billing records is slightly uncomfortable, because it’s important not to forget to press the "Apply" button after making changes in a record.
6.10. Journals.
While creating a journal, you specify its name, period of data writing to the disk and billing scheme.
When the records are stored, you can generate reports for selected periods and users who were active in that given period. These reports can be exported into Excel.
That is from a specific rule that draws a conclusion into writing data about packets to a specific journal or not, if the information in which this data should be written is undefined (e.g. while appearing a packet doesn’t belong to any connection). In this case, the information about the packet is written to a journal "Unknown" if it exists.
6.11. Users.
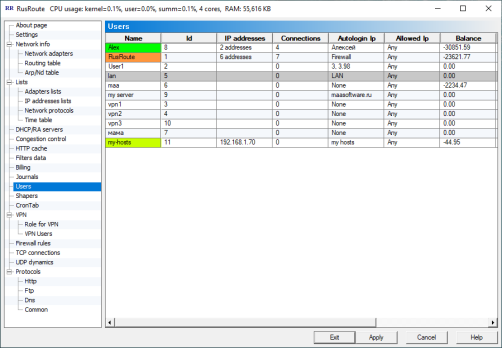 UsersList
UsersList
In the main window of the user account list you can see short description and activity (background changes the color), IP address(es) from which the user has been entered to the system and current balance.
You can logout every or all users or set balances per batches (for example, at the beginning of each month).
6.11.1. User info dialog.
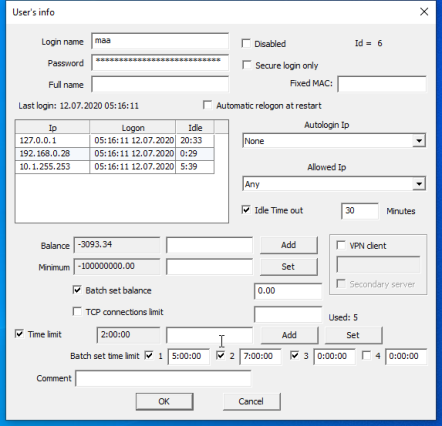 RusRoute firewall 2.0.7 - Time limit
RusRoute firewall 2.0.7 - Time limit
The main user info consists of login name and password, used when entering the system. Login is done through a web interface on port 10000 of the firewall’s protocol http. For example you can use the link http://127.0.0.1:10000 to login from the firewall, but for LAN computers you can use http://192.168.100.1:10000 , if the address of the firewall is 192.168.100.1. In the last case you need to allow access from unauthorized users' IP addresses to firewall on port 10000 TCP.
You can use special Win32 Application RRClient.exe to enter into the RusRoute system.
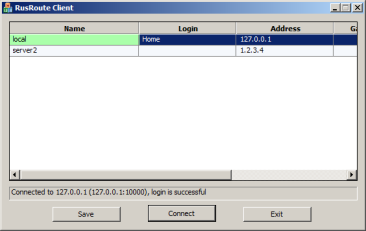 RRClient
RRClient
In this case protected login is used, RRClient tests every request from 2 to 2 minutes to support (keep alive) your connection. If there are 5 minutes of RRClient.exe inactivity (for example, if the network cable is detached from client's computer) RusRoute disconnects the user connected from that IP address. You can send text message from RusRoute to user on the UDP port 10007, witch is to be shown by RRClient.exe. RRClient needs to be configured to work with the server. A new record is described by address of server, port (10000), gateway (optional, this gateway is to setup up default gateway with metric 20), start up page (optional), which opens when you’ve successfully logged in to the system. At first you must load (update) keys from the server. This key is a public key, generated in the page "VPN role". RRClient (by choice) saves on disk the user name and password used to connect to the RusRoute server, encrypting data on the key related to the serial number of system partition.
Additional information about user is full name, id, "Disabled" feature, "Automatic re-logon at restart" feature, fixed IP address(es) from which the user works without entering username and password, allowed IP address(es) login through web interface is allowed, idle timeout (in minutes) for exceeding that automatic logout is performed, balance, minimal allowed value of balance when user work is still permitted, batch set balance option with its value, TCP connections limit option and comment.
You can increase or decrease a user’s balance by some value by specifying this value with a + or - sign and pressing the "Add" button.
Minimal allowable balance is set up by entering appropriate value and pressing the "Set" button.
6.12. Shapers (disabled in 3.0.2+ version).
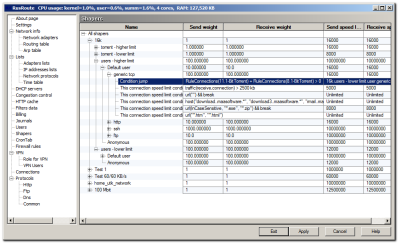 ShapersList
ShapersList
Shapers is an option of the algorithm managing priorities and speeds receiving/transmitting useful data of TCP protocol. It works on a socket layer and does not drop packets or affects connection quality.
Every shaper is described by four parameters: weights and maximal speed limits for transmitting and receiving. The exception is for root shapers for which weights are absent.
Shaper weight is the priority of the current connection or group of connections compared to other connections and group of connections on the same layer.
Maximum speed is a simple speed limit for the connection.
For shaper tuning you need to set up maximum allowed speed limits for root shapers (near to real limits). On the other hand, child shapers for the anonymous default user, selected users and simple sub shapers specify its weights, so you can enter the maximum speeds either by typing simply big values or values of additional restrictions.
In order for the shapers to be active you need to specify their usage in the protocols list while editing particular rules. If you’re using just one shaper for all protocols, you can only use the default shaper. The usual name of shaper shaper in the rule protocol list - <some_name>.user
The speed of a particular connection can be changed dynamically by adding The shaper’s speed limit conditions. The conditions can be defined as an arithmetical expression in the style of C/C++ by using calls for the next functions:
- RuleConnections(RuleName) - returns the number of active connections, allowed by a given rule name.
- ShaperConnections() - returns the number of active connections, attached to this shaper.
- ShaperConnections(recursive) - returns the number of active connections, attached to this shaper and its sub shapers.
- Time(Connection/SinceShaperAttached/AllShaperConnectionsRecursive) - returns the time since the connection is established/since shaper is attached (for a conditional jump, for example)/time since shaper is created.
- V(Connection/SinceShaperAttached/AllShaperConnectionsRecursive, Send/Recv/Send+Recv, 120s/120m/120h/183d), Traffic() with the same arguments - for obtaining average speed or data transferred size for particular connection since it is established or attached to a shaper, or sum for all connections of given shaper, sending or/and receiving data in a given time interval or for the all period if a parameter is missed. Time can be set in seconds, minutes, hours or days, the maximal allowed data values are given in the above example.
- url(InCaseSensitive, "http://*.iso", "*.rar") - the comparison of URL address string of HTTP-request with template mask through symbols '*', '?', where '*' represents an arbitrary number of any symbols (>= 0), '?' - any symbol. The InCaseSensitive parameter is used to compare without taking care of symbol registers.
- host("download.maasoftware.*", "rmail.maasoftware.*", "rmail.rusroute.*") is similar to a host name.
- false, true - boolean false and true.
- break - the equivalent of true but the other shaper conditions are not calculated in this case.
And operators
- "(" - Opening parenthesis
- ")" - Closing parenthesis
- "*" - Multiplication
- "/" - Division
- "%" - Modulus
- "+" - Addition
- "-" - Subtraction
- "<<" - Left shift
- ">>" - Right shift
- "<" - Less than
- ">" - Greater than
- "<=" - Less than or equal to
- ">=" - Greater than or equal to
- "==" - Equality
- "!=" - Inequality
- "&" - Bitwise AND
- "^" - Bitwise exclusive OR
- "|" - Bitwise inclusive OR
- "&&" - Logical AND
- "||" - Logical OR.
with an operator precedent in the order in which they exist in the above mentioned list (standard for C/C++).
Numerical expressions - integer numbers (qword) with the next possible modifications
- "B/s", "KB/s", "MB/s", "GB/s", "TB/s" - for speed
- "B", "KB", "MB", "GB", "TB" - for traffic volume
- "s", "m", "h", "d" - for the time. The time can be given in a union of values without explicitly giving the '+' operator, 2m30s means 2*60+30 seconds for example, and in a form of XX HH:MM:SS - XX days, HH hours, MM minutes, SS seconds, and the first zero parameters can be discarded.
The conditional jumps between shapers and can be used to change parameters of a given shaper (weight, speed limit).
Shapers are working well on fast channels.
6.13. Cron tab page.
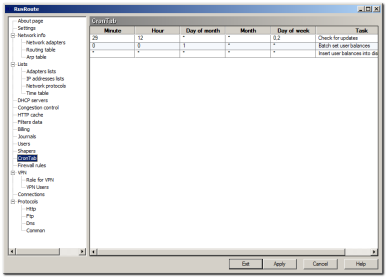 CronTabPage
CronTabPage 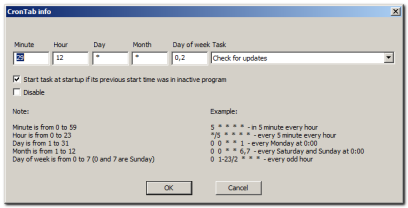 CronTab
CronTab
The cron tab allows you to start some actions in the program at a certain time (periodically, by schedule).
You can see in picture 2 how to set a new user balances automatically at beginning of each month.
6.14. Firewall rules.
RusRoute firewall rules are setting up as the first packet is passing for TCP/bidirectional UDP/ping connection. The rules for the other protocols (for unicast UDP) are setting up as is, using the packets data criteria, for transferring for each direction. It is need to set up both rules for packets passing to both directions for other IP protocols, GRE and IGMP for example. PPTP filter is not functional without of existence of additional rules for GRE.
Firewall rules are described by
- name
- list for source adapter
- list for source IP address
- user names
- list for destination adapter
- list for destination IP address
- protocols (with possibility to set shaper for every protocol)
- journal
- special options
- action
- additional comments.
- the rule can be the Splitter type to switch between alternatives for xmit packets for typical usage (union) some data transfer channels for VPN UDP traffic.
Special options represent the
- possibility to redirect to a special IP address and port (for example, you can set up an operating system for a client's computers with the option of DNS server IP address is IP address of RusRoute firewall and make the firewall rule to redirect DNS requests of users to an external DNS server of the provider),
- NAT - Network address translation - the technology that allows users to work in your local network as from the only IP address, allows you to work in the Internet. Appropriately, the rules describing a connection set up from local network to the Internet usually must have such an option. If you are using NAT for LAN then it is preferred to use the same technology for connections From the local RusRoute firewall to the Internet so that you avoid collisions with port numbers. In the current version NAT works for protocols TCP(FTP, etc), UDP and PING. Usual routing works for the same protocols with additions for the ICMP protocol. For other IP protocols incoming packets are simple accepted or sent by the firewall.
- Xmit (send) through adapter or gateway - if some default routes are used, and you can select here The adapter or gateway to transmit packets to an external network (it is useful for sat Internet if you want to route mail protocols (POP3, SMTP), more protected channels). Use Xmit to specific adapter and optional gateway for changing default route.
- keep source adapter - helper option, sometimes it’s useful to know though what adapter are the replies sent. In some cases, the firewall can ignore this option.
- don't duplicate Broadcasts on VPN adapter - send to VPN channel or send to Bridged LAN only.
- broadcast retranslation.
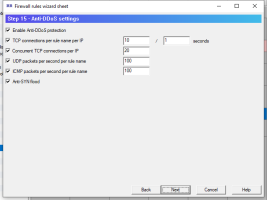
- Anti-SYN flood protection to block the attack of incoming tcp packets for a connection establishment; protection parameters are set up in Settings page.
- TCP connection limit - sets up a limited number of simultaneously working connections per rules with the same name.
- user is on the final IP - points to that fact is identification of user is to be found for destination point of packets, not for source. It is useful for LAN servers offering their services for Internet.
- when the user is logged on the final IP the rule is active.
- reverse NAT - for servers, for example, FTP, which belongs to the inside LAN, accessing it from the Internet.
- acting in the case of rule parameters counter exceeded in 15 minutes (for ports protection). If number/ip is specified then multiply counters will be used by not only rule name key but packet IP address too.
- TCP congestion control and avoidance algorithms for primary connections (connection from initiator) and for secondary connection (for response servers).
- disable this rule - to ignore rule from consideration of appropriate rules for connection.
If you need you can create splitter after the splitting rule, and some number of alternative splitting rules after the splitter (see picture 3) with the same name as the main splitting rule. The first rule is choosing at the first matching, the first alternative rule at the second and so on, cyclically.
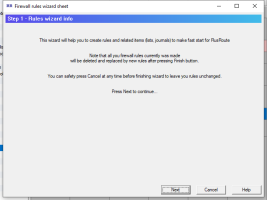
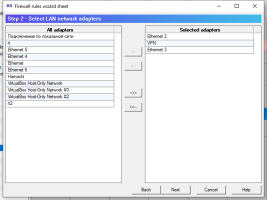
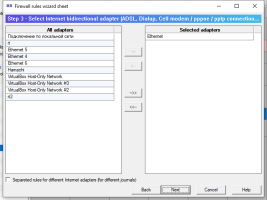
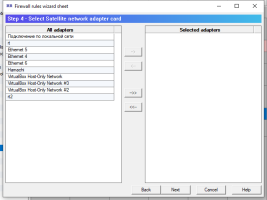
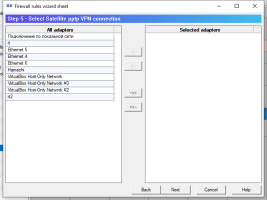
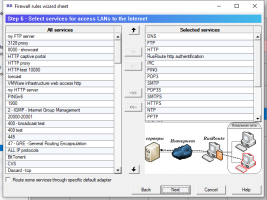
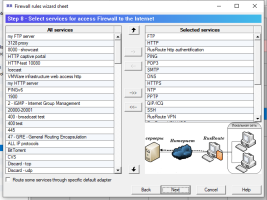
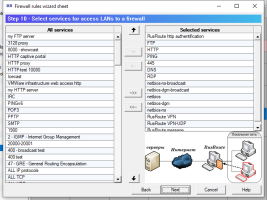
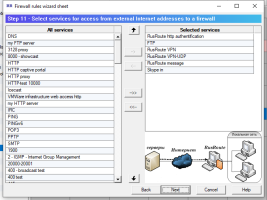
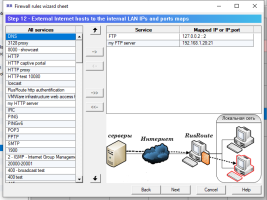
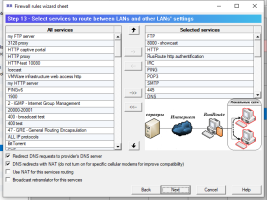
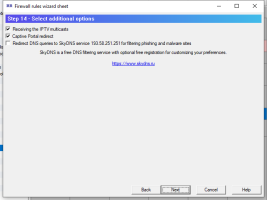
6.14.1. Firewall rules wizard.
Firewall rules wizard allows you to step by step answer configuration questions to create, usually, an initial set of firewall rules.
6.15. VPN.In this page group you can see the settings for creating a new virtual private network (VPN).
6.15.1. VPN role.
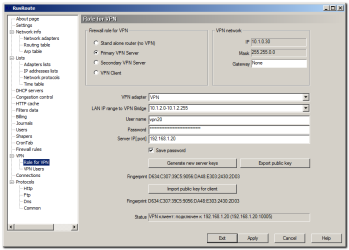 VpnRolePage
VpnRolePage
Here the main VPN settings are described:
VPN type:
- Stand alone router (no VPN) - the VPN functions are disabled.
- Primary VPN server - RusRoute starts on the computer TCP server on the port 10005 and UDP server on the port 10005 To serve VPN clients requests. Enter a valid user name and password so that the current computer is visible as a VPN client, and simply enter 127.0.0.1 for the address of the server
- Secondary VPN server - RusRoute makes a VPN connection primary or the other secondary; VPN server entered below, with entered parameters of user name and password, and starts TCP server on TCP port 10005 and UDP servers on the port 10005 (VPN server) and on the port 10004 (VPN client) to accept other user’s connections through server (which is named by the secondary server) to primary server. It’s more convenient to use secondary servers because you can connect two remote offices with a virtual network, since you are starting secondary VPN server in the second office, which splits loading on the VPN network, so that if two VPN users are connected to the same secondary VPN server, they are exchanging messages and their messages are routed directly from one client to the other through their secondary server, not through the primary VPN server.
- VPN client - usual VPN client, connected to primary or secondary VPN server, uses TCP connection to VPN server and creates UDP server on the port 10004 to receive VPN packets. UDP connection is not used in for special options if the "Settings" page is selected ("TCP only VPN"). This can be useful for compatibility, but VPN works slower and the VPN control connection can be overloaded if this option is turned on.
VPN network (information obtained by VPN adapter while using DHCP service):
- Virtual IP address of VPN client
- VPN network mask.
- Gateway - optional, here you can set the virtual address of some VPN clients to use it as a default gateway (for example, remote access to the Internet from another remote network). It might be necessary for you to set up routes with the help of your system program route.exe or special RusRoute firewall rule options to access the Internet correctly (for VPN connections). See also: route /?
The other settings:
- VPN adapter - please select VPN adapter from the list. VPN adapter is added to the system while RusRoute sets up.
- LAN IP range to VPN Bridge - if you’re using a VPN adapter as a real adapter, not virtual Ethernet adapter added to system while RusRoute sets up, and if the network of the real adapter is using an allowed IP addresses (network 10.1.0.0, mask 255.255.0.0), then you can set here the ranges and lists of IP addresses, which will be accessed for other VPN clients and their networks as Ethernet bridging. For example, you can set here 10.1.2.0-10.1.2.255,10.1.1.11 for one VPN client and 10.1.3.0-10.1.3.255 for another. For this situation, users from IP addresses 10.1.2.0-10.1.2.255 and 10.1.1.11 can exchange data with users from addresses 10.1.3.0-10.1.3.255 and other VPN clients too as they are located in the same Ethernet segment. You can use special firewall rules to set up duplicates incoming broadcast features to local VPN client and attached bridged LAN. See "Special" firewall rules for settings.
- User name - enter the user name to access the virtual protected network. Only users that can work on the primary server as VPN clients or secondary servers, can enter to VPN network.
- Password - the VPN password.
- Server IP[:port] - IP address or domain name of server, optionally colon and TCP port number for connection, if it differs from the default value - 10005. We recommend for the local primary VPN server to enter address 127.0.0.1.
- Save password - is to save password in config (in weakly protected text), otherwise the password is asked each time you connect.
- Generate new server keys - to create new keys (public and private) for using authorization and transferring temporary key of user to server. This you have to done before first use of primary VPN server. In the case of discrediting of key you have to stop primary VPN server (enter to stand alone router mode (no VPN)), generate the keys, launch VPN server again. There’s no need to generate keys for VPN users.
- Export/import the public key - it can be the safest way of transferring a public key from the server to a client (if, of course, you are trusted to courier or somehow deliver to transfer the key). You can verify the keys by fingerprint.
- Status - status line shows a connection to a server status or progress of keys generation.
Temporarily keys of VPN users are updating every 15 minutes.
6.15.2. VPN users.
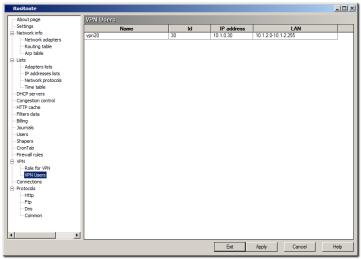 VpnUsersPage
VpnUsersPage
Here is show of the list of all connected VPN users. You can select the most typical actions with their IP addresses: ping, ftp, the view by Internet Explorer and explorer, viewing of remote desktop, copying of IP address, name and DNS name to clipboard. In the case of using "DNS" filter for a DNS protocol, than you can resolve IP address of VPN user with the name "user" by special DNS name "name.vpn". RusRoute will respond the appropriate request with returning VPN user IP address.
6.16. TCP connections.
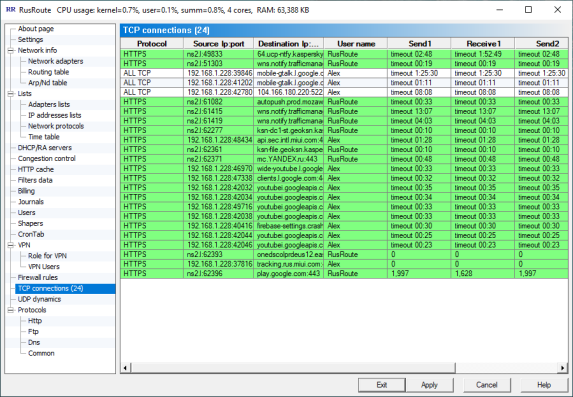 Connections
Connections
Showing TCP connections with parameters such as protocol, address, port, user name, speed of receiving/sending the primary(1) and secondary(2) levels, length of data transferred and rule name.
6.17. UDP dynamics.
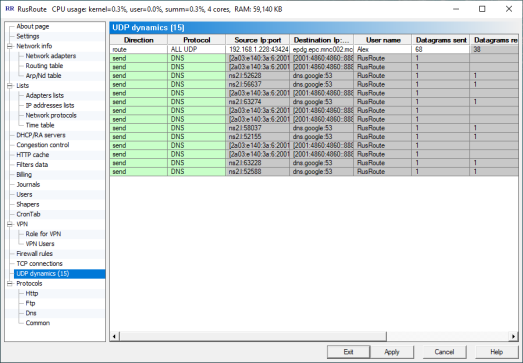 UDP dynamics
UDP dynamics
Showing UDP dynamic rules' connections with parameters such as protocol, address, port, user name, number of packets, length of data transferred and rule name.
6.18. Logs.
The most useful and interesting records about this processes in the network and inside the RusRoute firewall.
6.18.1. Http logs.
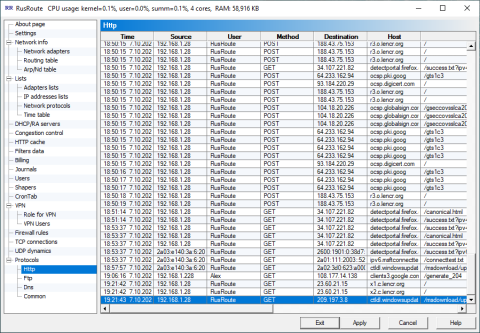 HttpProtocol
HttpProtocol
It shows parameters of requests for http protocol (it acts only for protocols which have set up filter type HTTP).
6.18.2. Ftp logs.
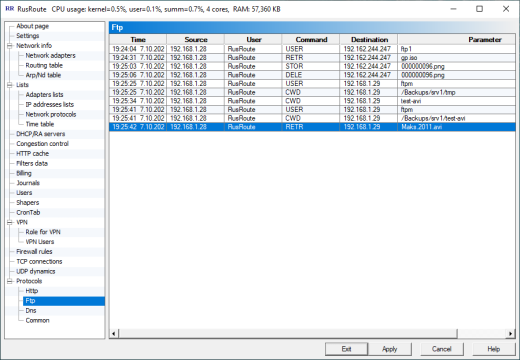 FtpProtocol
FtpProtocol
It shows some commands and their parameters for ftp protocol (it acts only for protocols which have set up filter type FTP).
6.18.3. Dns logs.
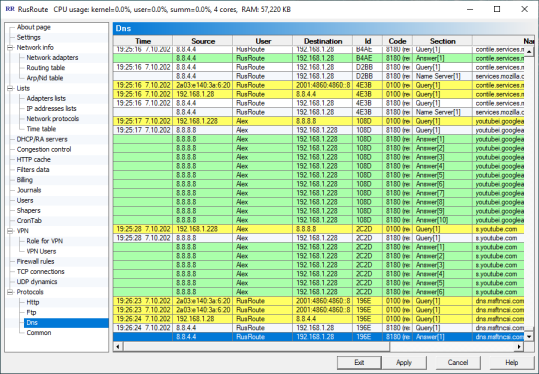 DnsProtocol
DnsProtocol
It shows the information about DNS queries and answers (it acts for protocols which have set up filter DNS).
6.18.4. Common log.
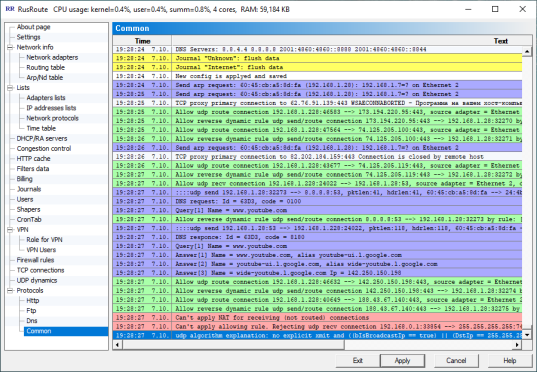 Protocol
Protocol
The most reach log of firewall working.
Messages are displayed in English preferably.
For example, message "Reject ... connection ... by rule: Default blocking rule, protocol: Unknown" is mentioned that there are no rules found in your rule list from the first rule to the last which is matched by current packet or connection, and as a result that packet/connection was blocked.
7. Technical support of the program.
Technical support of the program is making by e-mail: support@rusroute.com, and through forum of site http://rusroute.com/. [Eng], and by sites http://maasoft.org , http://rusroute.ru , http://maasoft.ru [Rus].
Ratio: